Zcoin is the first implementation of the Zerocoin protocol which uses Zero-Knowledge Proofs to assure a complete financial privacy and anonymity of the blockchain. As a privacy coin, Zcoin needs to protect your personal information such as the IP address, which can be linked to transactions and other addresses on the blockchain. This type of link ability is mitigated through the usage of TOR/I2P/VPN. It is important to note that Bitcoin and Zcoin transactions don’t contain any IP addresses. The only place, which is able to store that kind of personal information are the nodes in the P2P network. When the transaction is relayed from one node to another, there is no way to identify it as the original broadcast, but some suppositions could be made such as which IP is the one that the transaction is broadcasted from. A research done by Alex Biryukov, Dmitry Khovratovich and Ivan Pustogarov (Deanonymisation of Clients in a P2P network) suggests that the usage of TOR itself isn’t enough to hide identities and this is where Dandelion comes in.
What is Dandelion? And what does it add to privacy?
Researched by Giulia Fanti, Shaileshh Bojja Venkatakrishnan, Surya Bakshi, Bradley Denby, Shruti Bhargava, Andrew Miller and Pramod Viswanath and published here, the Dandelion is a lightweight cryptocurrency networking which adds privacy to the network by concealing the IP address of a transaction broadcaster. In blockchains such as the Bitcoin one, your transaction is broadcasted to all the nodes that you are connected to and they will further relay it to all the other nodes which aren’t connected yet. This method of propagation is known as ‘Bitcoin’s gossip protocol’. The problem that arises from this method is that if someone has control over enough nodes, he can track how the transaction travel through the network, respectively can estimate the IP address that originated the transaction.
Where is the difference?
The principle on which Dandelion works is modifying the communication between the nodes. This is done in two steps – the stem phase and the fluff phase.
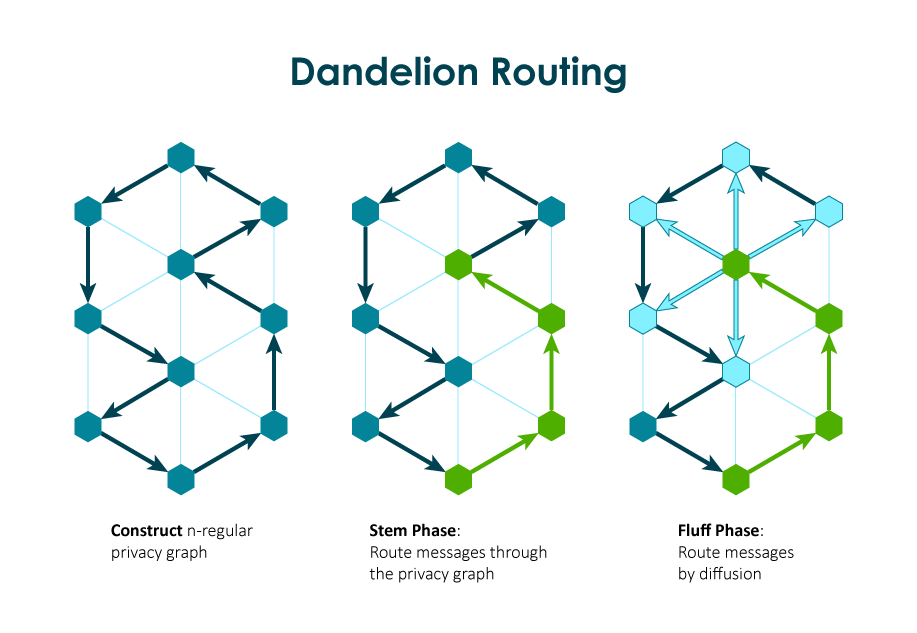
- Stem phase – the transaction is relayed to a node, instead of all the nodes connected, then it gets broadcasted from node to node.
- Fluff phase – this phase is initiated at a random time and sets back the transfer method to a gossip mode by telling all the connected nodes about the transaction.
This way even the node that ‘gossiped’ first is determined, that wouldn’t be necessarily the one that originated the transaction because it had jumped through several other nodes during the stem phase. The first nodes in the stem phase do not expose the transaction, until the randomly chosen moment. Then they enter the fluff phase and start broadcasting the transaction to all connected nodes.
Conclusion
As stated in the research above, attacks are possible, which can cause nodes to reject or blacklist the Tor connections, which will deanonymize the transactions. Dandelion complements Tor by providing further network layer anonymity for transactions on the blockchain, so even without Tor, Dandelion provides a good level of protection.
Zcoin is set to release the Dandelion integration in August 2018, right after the initial testing is complete.